Deployment Strategies and Circuit Breaker Pattern in Istio: A Comprehensive Guide
Istio simplifies traffic management, observability, and security for microservices architectures. As applications scale, implementing advanced deployment strategies and resilience patterns becomes essential. This blog covers two critical concepts: deployment strategies (with a focus on Canary Deployment) and the circuit breaker pattern, along with their implementation in Istio. We’ll also take a deep dive into Virtual Services and Destination Rules, the backbone of Istio’s traffic management system.
Deployment Strategies in Microservices
A deployment strategy defines how new versions of applications are released in a production environment with minimal risk. Common strategies include:
- Rolling Deployment: Incrementally updating a service version.
- Blue-Green Deployment: Maintaining two versions (live and new) and switching traffic once the new version is tested.
- Canary Deployment: Releasing the new version to a small subset of users to test its performance before full rollout.
Canary Deployment: An Overview
Canary Deployment allows gradual rollouts by directing a small percentage of traffic to a new version (canary) while most users continue to use the stable version. If the canary version performs as expected, traffic is progressively increased.
Benefits of Canary Deployment
- Early detection of issues in the new version.
- Reduced risk of affecting the majority of users.
- Fine-grained control over rollouts using metrics and monitoring tools.

Implementing Canary Deployment in Istio
Istio provides a robust way to manage Canary Deployments using Virtual Services and Destination Rules, which control traffic routing between service versions.
Understanding Virtual Services and Destination Rules
Istio’s traffic management capabilities rely on two key configurations:
- Virtual Service: Manages how requests are routed to services. For example, a virtual service can route 10% of traffic to a new service version and 90% to the existing version.
- Destination Rule: Specifies policies for traffic routed to a service, such as load balancing, TLS settings, or connection pool limits.
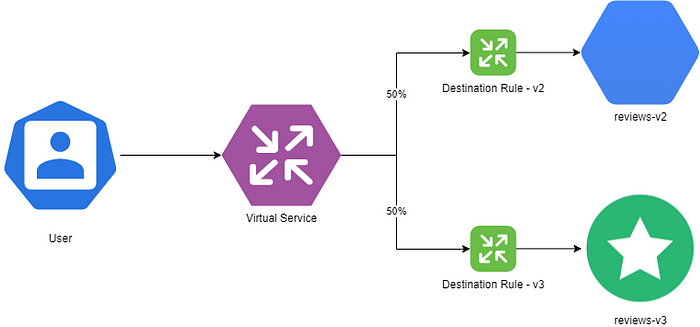
Example of Canary Deployment with YAML
Virtual Service YAML:
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: reviews
spec:
hosts:
- reviews
http:
- route:
- destination:
host: reviews
subset: v1
weight: 90
- destination:
host: reviews
subset: v2
weight: 10This configuration routes 90% of traffic to v1 of the reviews service and 10% to v2.
Destination Rule YAML:
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: reviews
spec:
host: reviews
subsets:
- name: v1
labels:
version: v1
- name: v2
labels:
version: v2This rule defines subsets v1 and v2, which map to different versions of the reviews service based on labels.
Subsets in Destination Rules
In Istio, subsets are a critical feature of Destination Rules. Subsets enable fine-grained traffic routing by grouping service instances based on labels. Each subset maps to a specific version of a service (e.g., v1 or v2), allowing Istio to direct traffic selectively.
How Subsets Work:
- Label Matching: Subsets are defined using labels in the Destination Rule. Each subset corresponds to a group of pods with a specific label.
- Version-Specific Traffic: Virtual Services use subsets to direct traffic to specific versions of a service.
- Granular Control: Subsets enable the application of different policies, such as timeouts or retries, to different service versions.
For example, in a deployment with two versions of a service (v1 and v2), subsets are defined in the Destination Rule to distinguish between the two versions
Deploying Canary with Kiali
Alternatively, you can configure Canary Deployment using the Kiali UI:
- Open Kiali and navigate to the service.
- Select the Service and click on it.
- At the top right corner click on
create weighted routing& Define traffic distribution (e.g., 90% to v1 and 10% to v2). - Monitor live traffic flow and adjust percentages as needed.
Circuit Breaker Pattern
Microservices architectures are susceptible to cascading failures, where the failure of one service triggers failures in others. To prevent this, Istio implements the circuit breaker pattern.
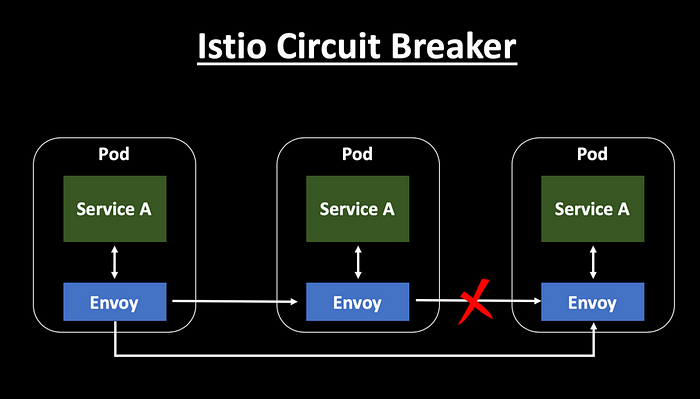
What Is the Circuit Breaker Pattern?
A circuit breaker detects failures in dependent services and limits further requests. It functions in three states:
- Closed: Traffic flows normally until a failure threshold is reached.
- Open: Requests to the failing service are blocked for a timeout period.
- Half-Open: A limited number of requests are sent to test if the service has recovered.

Implementing Circuit Breaker in Istio
In Istio, circuit breakers are configured using Destination Rules.
Example Circuit Breaker Configuration
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: reviews-cb
spec:
host: reviews
trafficPolicy:
connectionPool:
tcp:
maxConnections: 2
http:
http1MaxPendingRequests: 1
maxRequestsPerConnection: 1
outlierDetection:
consecutive5xxErrors: 2
interval: 10s
baseEjectionTime: 30sExplanation:
- Limits each connection to two concurrent requests.
- If the
reviewsservice encounters two consecutive 5xx errors within 10 seconds, it will be ejected for 30 seconds. - After 30 seconds, the circuit enters a half-open state to test recovery.
Circuit Breaker with Timeout
Istio also allows configuring timeouts to prevent requests from hanging indefinitely.
Example Timeout Configuration
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: reviews-timeout
spec:
hosts:
- reviews
http:
- timeout: 5s
route:
- destination:
host: reviews
subset: v1This configuration sets a 5-second timeout for requests to the reviews service. If the service does not respond within this time, the request will fail gracefully.
Architecture of Canary Deployment in Istio
Let’s break down the architecture of Canary Deployment in Istio:
- Service Versions: Two or more versions of a microservice (e.g.,
v1andv2). - Virtual Service: Routes traffic to different service versions based on defined percentages.
- Destination Rule: Maps subsets to service versions and applies traffic policies.
- Sidecar Proxies: Envoy proxies in each pod handle routing, metrics, and circuit breaking.
- Kiali Dashboard: Visualizes traffic distribution and application performance in real-time.
When traffic is routed to the canary version (v2), metrics and logs are monitored to ensure stability. If issues are detected, traffic can be reverted to the stable version (v1) by adjusting weights in the Virtual Service.
Summary
In this blog, we covered two critical concepts for microservices:
- Deployment Strategies: We explored Canary Deployment, its benefits, and its implementation in Istio using YAML and Kiali.
- Circuit Breaker Pattern: We discussed how to prevent cascading failures by configuring circuit breakers and timeouts in Istio.
- Subsets: We detailed how subsets in Destination Rules enable precise traffic routing and policy enforcement.
Key Takeaways
- Canary Deployment enables safe and gradual rollouts of new versions.
- Circuit Breakers improve system resilience by managing service failures effectively.
- Virtual Services and Destination Rules (especially subsets) are the foundation of Istio’s traffic management.
By combining these patterns and tools, Istio empowers organizations to build robust, fault-tolerant microservices architectures.
